MED Fadel Moumeni
LinkedinWelcome back! We’re continuing our series on SCADA hacking. This time, we’ll explore how I was able to take over a gas station during a penetration testing engagement.
During a penetration testing engagement, I gained access to the internal network and began discovering live hosts and IP addresses. Then, I ran a large-scale Masscan scan looking for specific web services running on various ports, such as 3000, 30001, and 8080.
I extracted all the IPs and piped them into httpx to quickly identify the services. I found multiple web services that caught my eye.
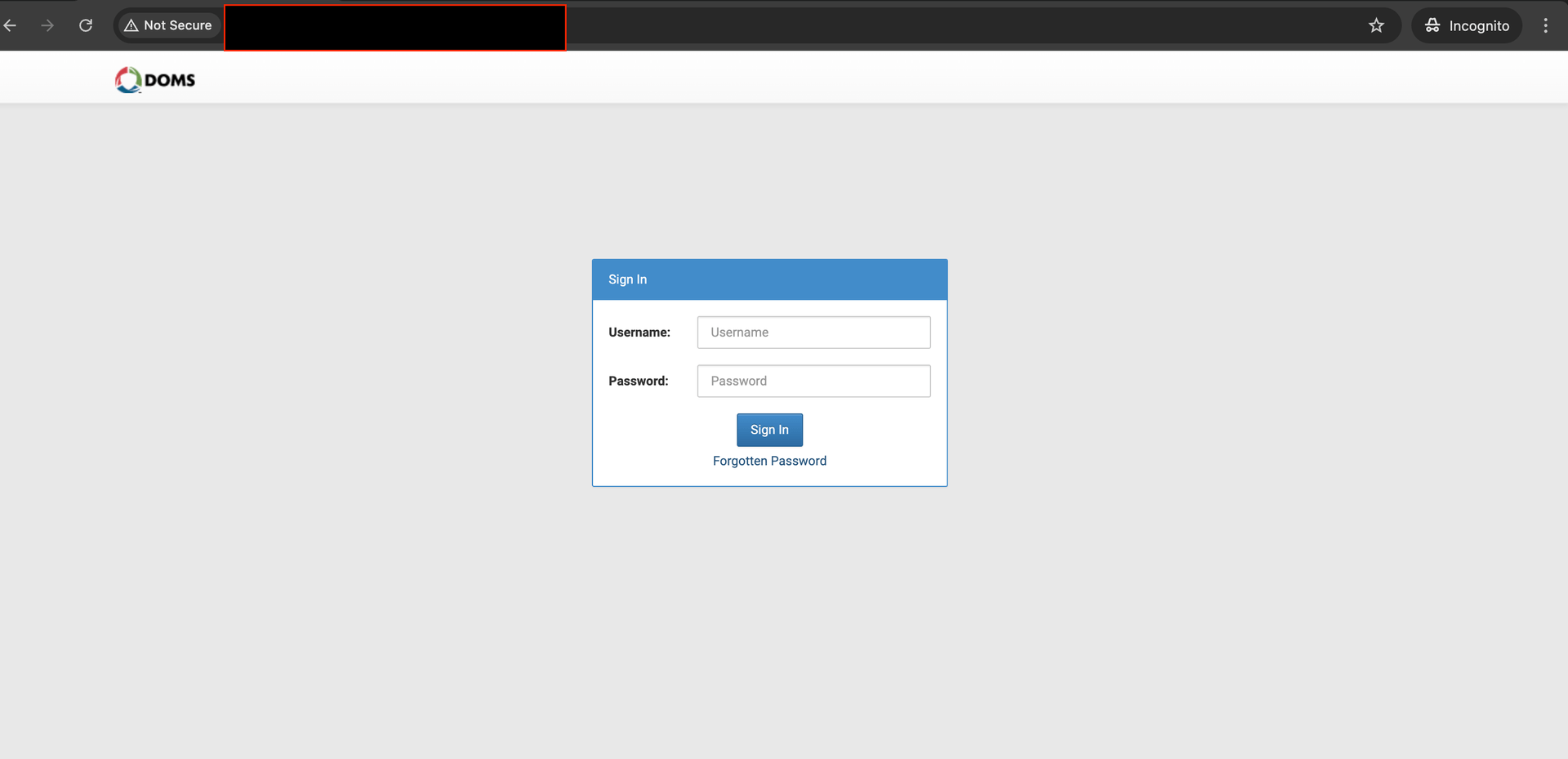
With a quick search, it appeared that these were web services related to the DOMS PSS 5000.
Most modern fueling stations rely on programmable controllers to manage fuel dispensing, monitor tank levels, and interface with payment systems. In this case, the central logic controller was a DOMS PSS 5000, a widely used automation unit designed to integrate pumps, sensors, and fuel inventory management into a single framework.
The DOMS PSS 5000 is the digital backbone of forecourt operations. It enables real-time control and status monitoring of pumps, tanks, and related systems while providing remote diagnostic capabilities. It is robust and popular, but like any solution it depends on secure configuration.
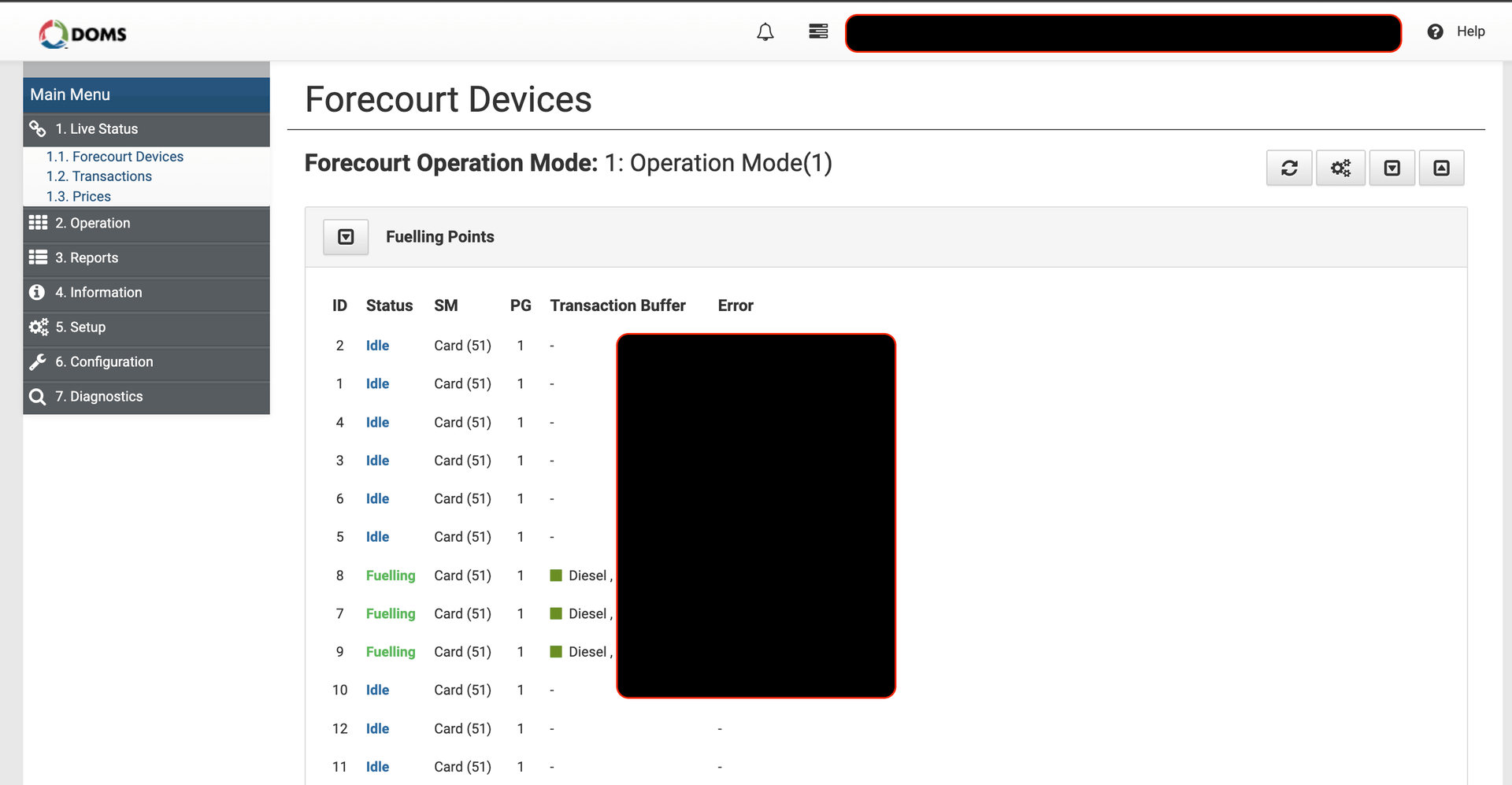
After investigating, it appeared that most devices had the guest login enabled, with guest/guest credentials that provided read-only permissions.
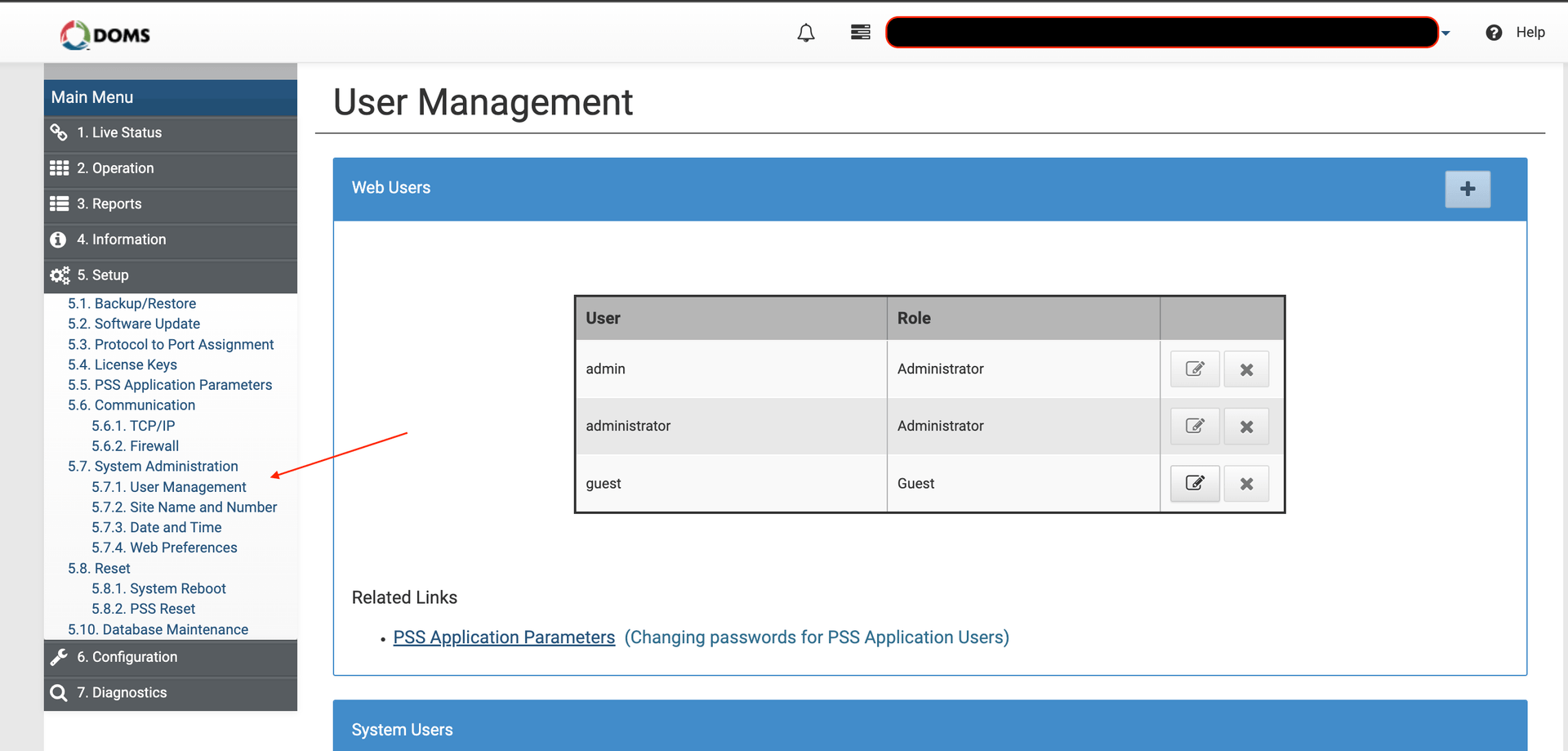
Navigating to User Management showed all users who had access, along with their roles. We’ll take advantage of this to brute-force the admin password.
A successful brute-force attack on the login endpoint allowed me to recover the admin password because it was weak. With admin access to DOMS, I had the privileges to change product prices, extract all transaction records, and even reboot the device.
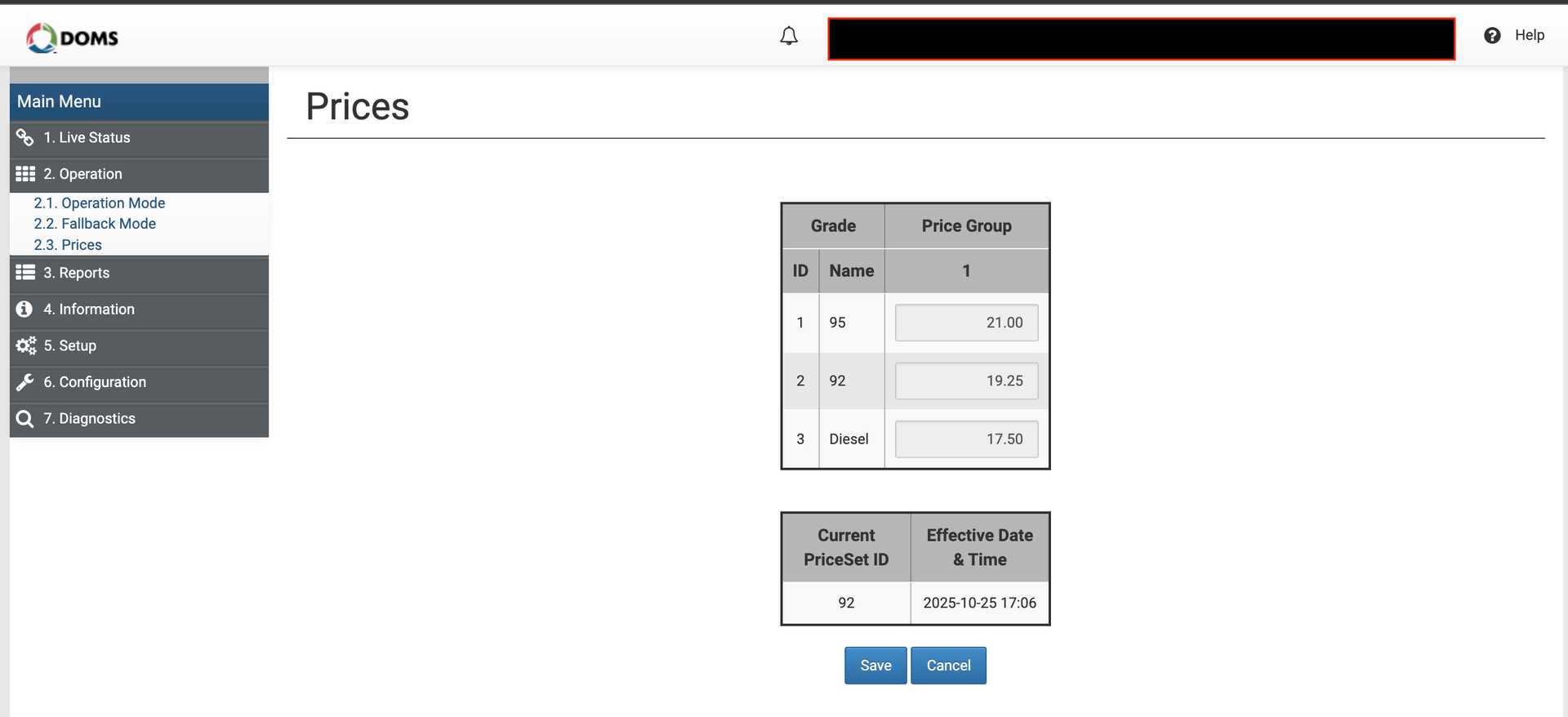
In brief, we took control of a gas station through default and weak credentials. Once we accessed the admin portal, we had the privileges to manipulate the prices of diesel, gasoil, and other related products, exfiltrate the full transaction history, and even reboot the system, which could disrupt the station’s operations.
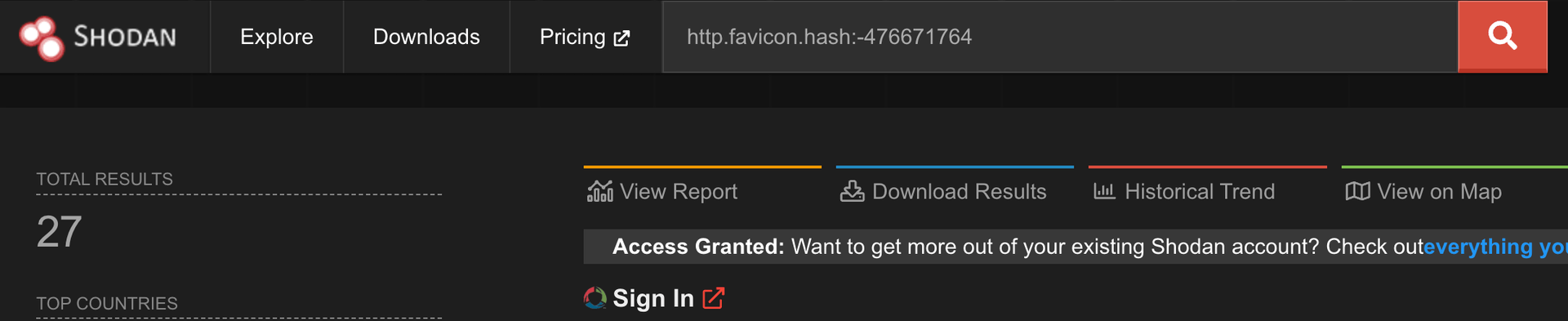
A quick search on Shodan showed that 27 DOMS PSS 5000 devices are exposed online, giving attackers the opportunity to exploit them and disrupt stations remotely.